Cyberattacks targeting local government organizations and critical infrastructure, such as water utilities, are no longer theoretical risks; they are escalating in both frequency and severity. The Environmental Protection Agency (EPA) issued an enforcement alert urging water systems to take immediate, decisive action to protect the nation’s drinking water, underscoring the heightened vulnerability of America’s public infrastructure.
While earlier cyberattacks often involved defacing websites or entering a provider’s network—modern threats are far more insidious. Attackers are now targeting core utility operations. According to the EPA, these intrusions can interfere with water treatment and storage, damage vital equipment like pumps and valves, and even manipulate chemical levels to hazardous extremes. The risk is not only service disruption but potential harm to public health.
In a digital arms race between attackers and defenders, AI-driven tools allow threat actors to scale their efforts rapidly, launching sophisticated, adaptive attacks that can bypass even well-established security measures. The result is a formidable threat capable of overwhelming municipal systems, halting operations, and extracting significant ransom demands.
Alarmingly, some recent breaches have been traced back to state-aligned threat actors. Countries such as China, Russia, and Iran have been identified as developing capabilities to disable U.S. infrastructure, including water and wastewater systems. Dawn Cappelli, a cybersecurity expert at Dragos Inc., warns that these nations often operate through proxy groups or hacktivist collectives. “By working behind the scenes with these hacktivist groups, now these (nation states) have plausible deniability, and they can let these groups carry out destructive attacks,” she explains. “That, to me, is a game-changer.”
Inside the Cybersecurity Gaps Threatening Public Utilities
Ransomware groups increasingly view water utilities as prime targets. These organizations are critical enough to compel quick payments, yet often operate on aging infrastructure and limited IT support. As a result, ransomware attacks are surging across the sector. Cybercriminals exploit outdated systems and single points of failure, triggering widespread disruptions.
Recent inspections back this up. Nearly 70% of utilities evaluated by federal officials in the past year were found to be non-compliant with cybersecurity standards designed to prevent intrusions. These gaps range from misconfigured networks to lack of even the most basic cyber hygiene. The EPA has called on even the smallest systems to invest in improved protections.
In some cases, the deficiencies are surprisingly simple. The EPA has reported instances where utilities failed to change default passwords or revoke access for former employees. Since utilities rely heavily on software and process control systems to manage operations, these oversights represent serious vulnerabilities that can be exploited with ease.
Deputy EPA Administrator Janet McCabe emphasized the urgency of integrating cybersecurity into everyday operations. “In many cases, systems are not doing what they are supposed to be doing, which is to have completed a risk assessment of their vulnerabilities that includes cybersecurity and to make sure that plan is available and informing the way they do business,” she said.
These systemic weaknesses have already been exploited. Across the country, real-world cyberattacks on local government organizations reveal the stark consequences of outdated technology, poor cyber hygiene, and underinvestment in digital defenses. The following case studies illustrate what happens when those vulnerabilities are left unaddressed.
Oldsmar, Florida
When Unauthorized Access Puts Public Health at Risk
In early 2021, the City of Oldsmar, Florida, became a chilling example of how vulnerable critical infrastructure can be to cyber threats. A plant operator noticed suspicious activity when his mouse cursor began moving across the screen without his input. Initially dismissing it as a routine remote login from a supervisor, he later watched in real time as the cursor navigated to chemical control settings and attempted to drastically increase the levels of sodium hydroxide—commonly known as lye—from 100 parts per million to a potentially dangerous 11,100 parts per million. Fortunately, the operator quickly intervened, reverting the settings before the change could impact the water supply.
While the FBI could not definitively determine whether the intrusion was malicious or simply an operational error, forensic analysis told a different story. Network logs confirmed unauthorized access through the remote desktop application TeamViewer. Despite initial speculation by city officials that employee error may have been to blame, the digital trail revealed a clear compromise of system access.
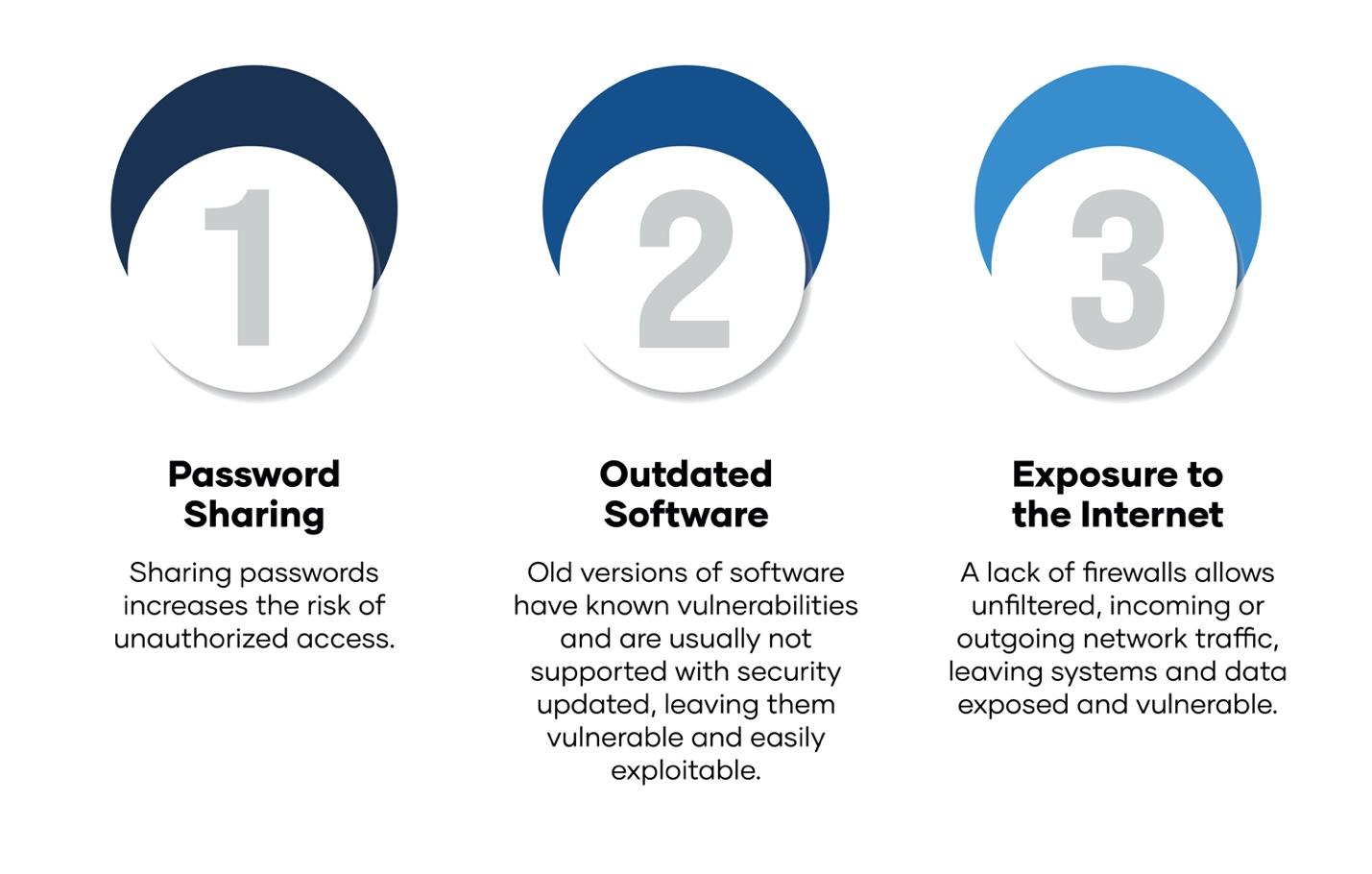
The conditions that made Oldsmar a target are alarmingly common among small utilities: all employees reportedly shared the same password for TeamViewer access, the plant’s computers were still running Windows 7—an unsupported operating system since January 2020—and there was no firewall protecting the network. These oversights enabled direct access to operational controls, highlighting the risks of outdated technology and weak cybersecurity practices. Oldsmar’s near miss demonstrates why even small communities must prioritize modern cybersecurity infrastructure.
Limestone, Maine
When Outdated Systems Open the Door to Ransomware
In July 2021, the town of Limestone, Maine, became another cautionary tale for municipal governments nationwide after its wastewater treatment facility fell victim to a ransomware attack. Criminal actors exploited remote access pathways to infiltrate the Supervisory Control and Data Acquisition (SCADA) system, deploying the ZuCaNo ransomware. This attack encrypted critical data, crippling the facility’s ability to monitor and manage wastewater treatment operations in real-time.
Following the ransomware infiltration, Limestone’s facility was forced to shift operations to manual control, relying on frequent operator rounds to maintain service continuity. The attack disabled a single SCADA computer running an obsolete Windows 7 operating system—a system already earmarked for replacement. Officials ultimately chose not to pay the ransom, recognizing the need to update the equipment regardless. However, the incident highlights a broader concern: many public entities continue to rely on unsupported or end-of-life technology, exposing themselves to avoidable cybersecurity risks.

North Texas
When Cyberattacks Disrupt Public Communications
Another striking example of escalating cyber threats in the public utility sector is the ransomware attack on the North Texas Municipal Water District (NTMWD), which provides essential services to over two million residents across 13 cities. A cybercrime group known as Daixin Team claimed responsibility for the breach, stating they had stolen more than 33,000 files containing sensitive customer information. The group also alleged they had accessed board meeting minutes, personnel records, audit documents, and internal project files, raising serious concerns about data privacy.
While NTMWD’s core functions—water, wastewater, and solid waste services—remained operational, the attack significantly affected the district’s IT infrastructure. Business systems were compromised, and although much of the network was restored relatively quickly, phone systems remained down for more than two and a half weeks. This prolonged outage disrupted communication and hindered the district’s ability to respond to customer needs, highlighting how cyberattacks can impair public trust and disrupt service delivery even when physical operations continue unaffected.
Although detailed technical disclosures remain limited, it’s believed that the attackers may have gained access through phishing emails designed to capture VPN credentials—a known tactic used by the Daixin Team. The group is also known to exploit vulnerabilities in VPN infrastructure, making it crucial for public sector organizations to fortify their digital perimeters. The NTMWD incident illustrates the importance of proactive cybersecurity measures, including employee training on phishing awareness and regular assessments of remote access security protocols.

Aliquippa, Pennsylvania
When Geopolitics Breaches the Local Level
Cyberattacks on public infrastructure are often viewed through a technical or criminal lens, but some incidents reveal deeper political motivations. In November 2023, an Iranian-linked hacktivist group known as Cyber Av3ngers infiltrated the Aliquippa, Pennsylvania water authority. The group compromised a Unitronics programmable logic controller (PLC) at one of the authority’s booster stations, disabling its automated control of water pressure and replacing the interface with an anti-Israel message. This politically charged intrusion marked a troubling escalation, where international conflict spills over into small-town America’s critical infrastructure.
Responding to an alarm triggered by the breach, crews swiftly shifted the system into manual operation, where it remained for at least two weeks until the compromised PLC was replaced and the evidence turned over to the FBI. The incident not only disrupted operations but caught local leadership off guard. Matthew Mottes, Chairman of the municipal water authority, candidly noted, “If you told me to list 10 things that would go wrong with our water authority, this would not be on the list.”
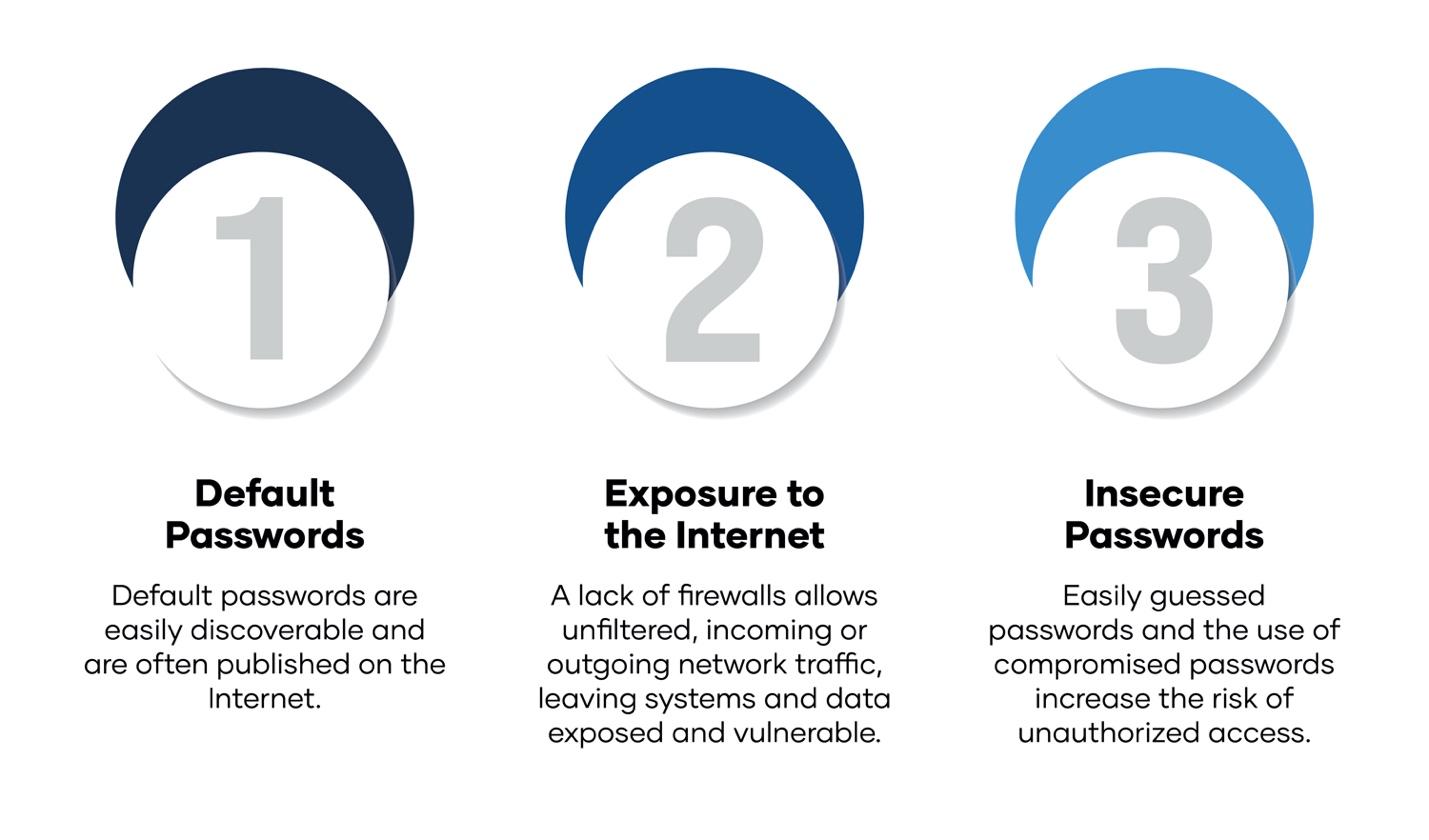
In the aftermath of the attack, an investigation by Summit Security Group uncovered that Cyber Av3ngers had initially targeted the Israeli manufacturer Unitronics. Through that effort, they learned to exploit vulnerabilities in the Unitronics Vision Series PLCs used in a variety of installations. The primary vulnerability they leveraged was a default administrative password—passwords that are easily found online and widely known among cybersecurity professionals. This oversight opened the door for attackers to gain immediate access.
In the case of the Aliquippa facility, the PLC was not only vulnerable due to its default credentials, but it was also directly exposed to the internet, drastically reducing the time and effort needed for cybercriminals to gain access. Internet-facing devices without adequate segmentation or firewall protections represent a critical weakness that can be addressed with simple yet essential best practices.
This wasn’t an isolated incident. The motivation—to protest Israel and Israeli-made technology—continues to drive similar breaches. As of February 2025, the FBI confirmed at least six additional compromises of water facilities across the United States that followed a similar pattern. Vulnerable Unitronics devices still remain exposed across the country, presenting an ongoing risk to public utilities.
Muleshoe, Texas
When Foreign Actors Seize Operational Control
In January 2024, Muleshoe, Texas, became another target in a string of geopolitically motivated cyberattacks. The Cyber Army of Russia Reborn (CARR), a group of Russian hackers claiming Kremlin backing, remotely accessed the town’s water utility software. By altering control system settings, the attackers caused tanks to overflow, spilling thousands of gallons of water over the course of nearly an hour. The impact wasn’t limited to Muleshoe—neighboring towns Abernathy, Hale Center, and Lockney were also affected. As a precaution, all three municipalities disabled their utility management software to prevent further manipulation.
Across the affected systems, the attackers maxed out control set points, turned off alarm mechanisms, and changed administrative credentials to lock out facility operators. These actions gave the hackers complete control over the systems. While the operational impact varied, with some facilities experiencing only minor tank overflows, many quickly transitioned to manual operations to regain stability and prevent more serious damage.
Although the incident did not lead to widespread or prolonged service outages, cybersecurity experts saw it as a test rather than an endgame. A representative from the Robert Strauss Center of International Security and Law at the University of Texas at Austin suggested that this intrusion may have been designed to assess vulnerabilities and response times. Since early 2024, both the Cybersecurity and Infrastructure Security Agency (CISA) and the FBI have responded to several similar attacks on water and wastewater facilities tied to pro-Russian actors.

The attackers used a range of techniques to infiltrate and manipulate the targeted systems. Chief among them was leveraging Virtual Network Computing (VNC) Remote Frame Buffer Protocol to access Human-Machine Interfaces (HMIs) and alter underlying operational technology. They commonly exploited Port 5900, using default credentials and weak passwords on systems that lacked Multi-Factor Authentication (MFA), granting them unfettered access to sensitive infrastructure.
Further investigation revealed that many of the compromised HMIs were unsupported legacy devices—foreign-manufactured systems that had been rebranded as U.S. products. This raises concerns not just about technical vulnerabilities, but also about supply chain transparency. The incident underscores the need for public sector organizations to thoroughly vet the origin, security, and lifecycle support of any operational technology they procure.
In response to these developments, the Environmental Protection Agency (EPA) and CISA published a fact sheet in December outlining key recommendations for securing internet-exposed HMIs. The guidance highlights the continuing risk posed by unsecured operational technology and urges public utilities to adopt strong access controls, audit systems regularly, and reduce exposure to the public internet. With the threat landscape evolving, these measures are critical to protecting essential services from politically motivated cyber intrusions.
A Shifting Threat Landscape for Local Utilities
The cyberattacks outlined in these case studies are not isolated incidents—they represent an accelerating trend. From politically motivated intrusions in Aliquippa and Muleshoe to financially driven ransomware attacks like those in Limestone and North Texas, the common thread is clear: public utility infrastructure is increasingly seen as both a soft target and a high-impact one. Adversaries are no longer just lone hackers or small groups. Today’s threat actors are often well-funded, state-aligned, and equipped with AI-enhanced tools capable of bypassing traditional defenses.
The examples also reveal that many vulnerabilities—default credentials, exposed devices, outdated software, and lack of network segmentation—are preventable. These are not failures of technology, but of prioritization. As EPA and CISA continue to raise alarms, the message to local government leaders is clear: cyber risk is no longer just a backend IT concern, but a frontline responsibility.
For municipal leaders looking to strengthen their cyber defenses, our recent blog post, Cybersecurity in the Water & Wastewater Sector, delivers a straightforward, actionable roadmap. Written with the realities of resource-constrained local governments in mind, it walks municipal leaders through key strategies recommended by Summit Security Group, empowering organizations to take immediate steps that enhance both operational safety and long-term resilience in the face of growing digital threats.


